Scheda Raspberry Pi Pico e rp2040: ethernet w5500 e requests HTTP e HTTPS (SSL)
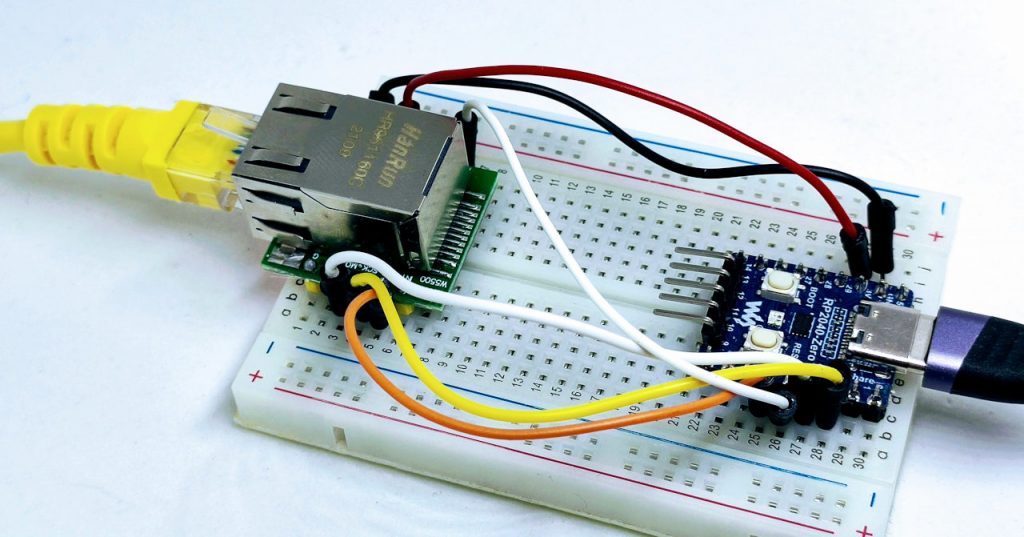
In questo articolo, esploreremo il modulo w5500 con le nostre schede rp2040. w5500 è un dispositivo abbastanza potente che consente una connessione cablata.
Cercheremo anche di dare una soluzione a un problema noioso: il dispositivo non fornisce una connessione SSL, e in un mondo affidabile come questo, è un altro grande limite, fortunatamente, OPEnS ha sviluppato un wrapper che contiene in un pacchetto tutte le implementazioni BearSSL, e questo, con una discreta quantità di risorse, consente all’Ethernet Arduino standard di utilizzare connessioni sicure.
Dispositivi
Il chip W5500 è un controller Ethernet TCP/IP cablato che fornisce una connessione Internet più semplice ai sistemi embedded. W5500 consente agli utenti di avere connettività Internet nelle loro applicazioni semplicemente utilizzando il singolo chip in cui sono incorporati stack TCP/IP, MAC Ethernet 10/100 e PHY.
L’Hardwired TCP/IP di WIZnet è la tecnologia che supporta i protocolli TCP, UDP, IPv4, ICMP, ARP, IGMP e PPPoE. W5500 incorpora il buffer di memoria interna da 32 Kbyte per l’elaborazione dei pacchetti Ethernet. Se utilizzi W5500, puoi implementare l’applicazione Ethernet aggiungendo un semplice programma socket. È un modo più rapido e semplice rispetto a qualsiasi altra soluzione Ethernet integrata. Gli utenti possono utilizzare otto socket hardware indipendenti contemporaneamente.
SPI (Serial Peripheral Interface) è fornita per una facile integrazione con l’MCU esterno. L’SPI del W5500 supporta una velocità di 80 MHz e un nuovo protocollo SPI efficiente per comunicazioni di rete ad alta velocità. Per ridurre il consumo energetico del sistema, il W5500 fornisce WOL (Wake on LAN) e la modalità di spegnimento.
Caratteristiche
- Supporta protocolli TCP/IP cablati: TCP, UDP, ICMP, IPv4, ARP, IGMP, PPPoE
- Supporta 8 socket indipendenti contemporaneamente
- Supporta la modalità di spegnimento
- Supporta Wake on LAN su UDP
- Supporta l’interfaccia periferica seriale ad alta velocità (MODALITÀ SPI 0, 3)
- Memoria interna da 32 Kbyte per buffer TX/RX
- PHY Ethernet 10BaseT/100BaseTX integrato
- Supporta la negoziazione automatica (Full e half duplex, 10 e 100-based)
- Non supporta la frammentazione IP
- Funzionamento a 3,3 V con tolleranza del segnale I/O a 5 V
- Uscite LED (Full/Halfduplex, Link, Speed, Active)
- Pacchetto senza piombo LQFP a 48 pin (7×7 mm, passo 0,5 mm)
Esiste un’ampia serie di dispositivi w5500, ma i più diffusi sono 2 in particolare.
Il meno costoso è il w5500 che vedete in foto.
Ma ora c’è una versione compatta denominata w5500 lite, molto interessante come dispositivo per la produzione.
Qui la mia selezione di dispositivi Ethernet w5500 lite - w5500 - enc26j60 mini - enc26j60 - lan8720
Collegamenti
Ecco la mia selezione di schede rp2040 Official Pi Pico - Official Pi Pico W - Waveshare rp2040-zero - WeAct Studio rp2040
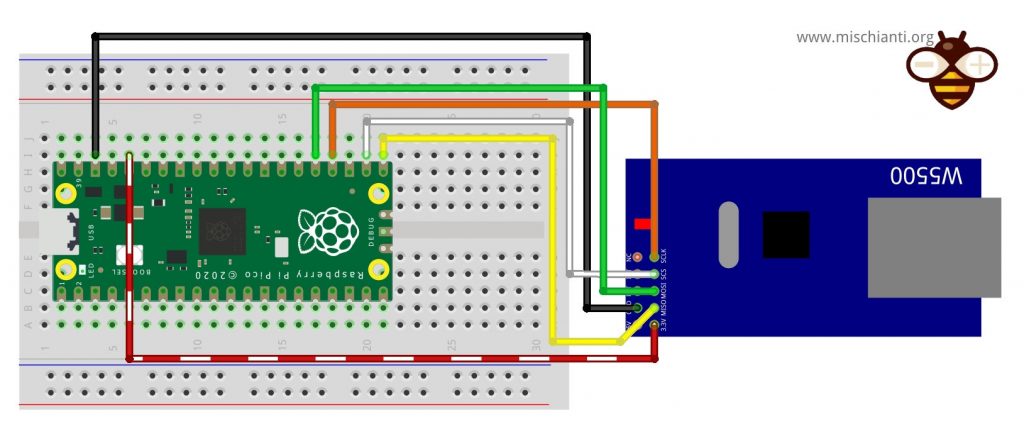
Questo dispositivo utilizza un’interfaccia SPI; per impostazione predefinita, utilizzerò un’interfaccia SPI di base.
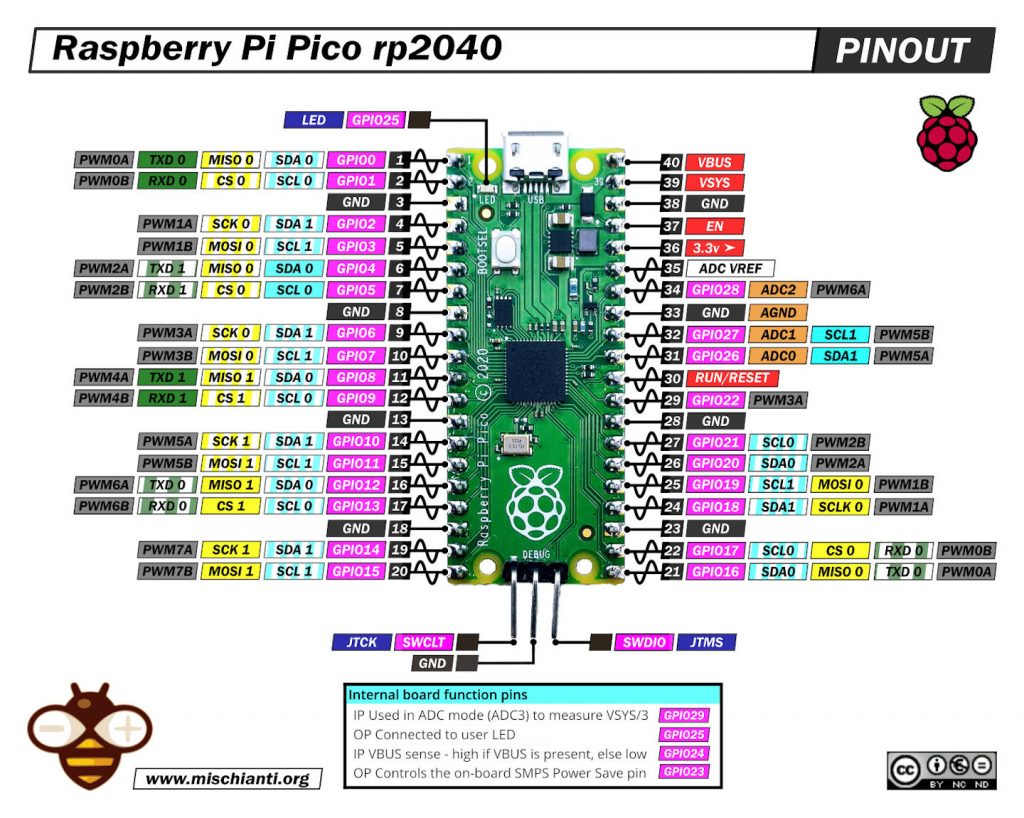
Raspberry Pi Pico
| Pico | w5500 |
|---|---|
| 17 | CS |
| 18 | SCK |
| 16 | MISO |
| 19 | MOSI |
| 3.3v (need >150mha) | VCC |
| GND | GND |
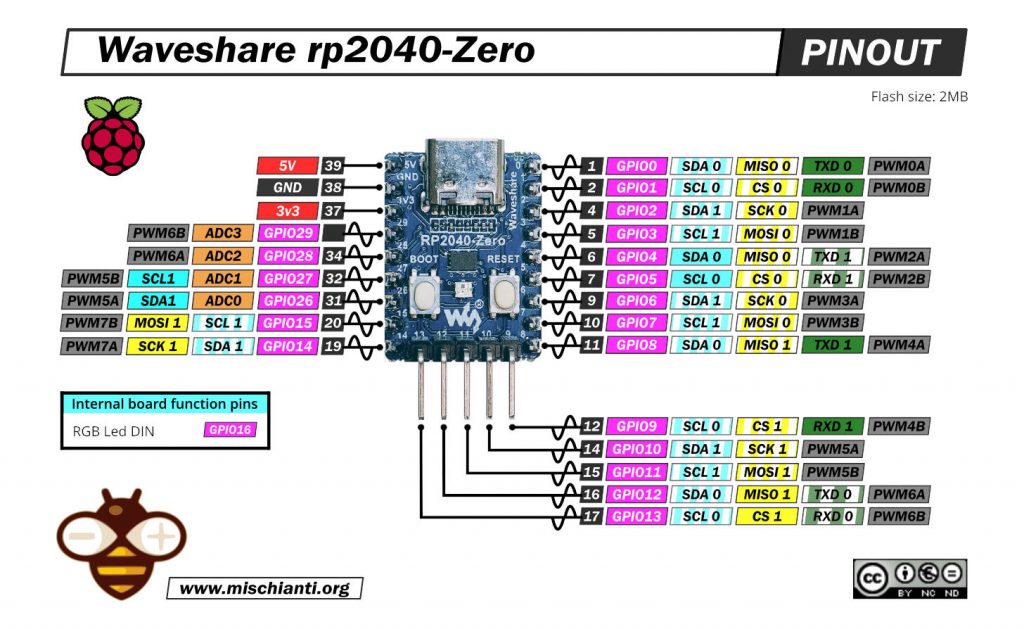
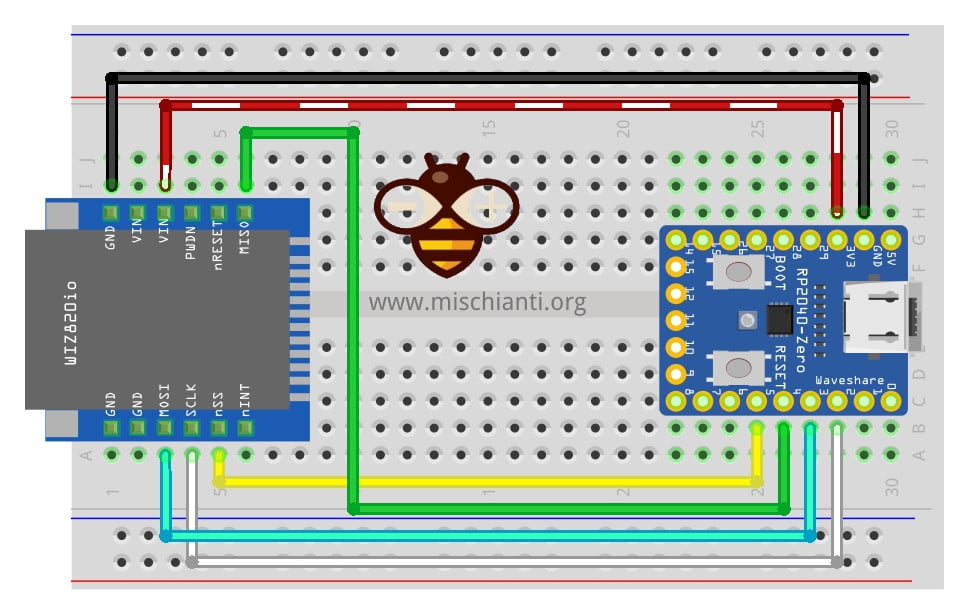
Waveshare rp2040-zero
Ricorda che il cablaggio per questo dispositivo si basa su un tutorial che puoi trovare qui.
| rp2040-zero | w5500 |
|---|---|
| 5 | CS |
| 2 | SCK |
| 4 | MISO |
| 3 | MOSI |
| 3.3v (need >150mha) | VCC |
| GND | GND |
Libreria
Esiste un’ampia selezione di librerie, ma quella standard è la scelta migliore. Puoi trovarlo nel gestore della libreria Arduino standard.
SSLClient
Questa libreria e questo dispositivo non supportano SSL, quindi aggiungendo queste funzionalità esiste una libreria alternativa denominata SSLClient che necessita di una piccola patch di Ethernet.
SSLClient aggiunge la funzionalità TLS 1.2 a qualsiasi libreria di rete che implementa l’interfaccia Arduino Client, comprese le classi Arduino EthernetClient e WiFiClient. SSLClient è stato creato per integrare TLS perfettamente con l’infrastruttura Arduino utilizzando il BearSSL come motore TLS sottostante. A differenza di ArduinoBearSSL, SSLClient è completamente autonomo e non richiede alcun hardware aggiuntivo (a parte una connessione di rete). (cit.)
Client SSL con Ethernet
Se stai utilizzando la libreria Arduino Ethernet, dovrai modificare la libreria per supportare le grandi dimensioni del buffer per le richieste da SSL. Puoi modificare tu stesso la libreria o utilizzare questo fork della libreria Ethernet con la modifica. Per utilizzare il fork: scarica una copia zippata del fork tramite GitHub, usa il pulsante “aggiungi una libreria .zip” in Arduino per installare la libreria e sostituiscila #include "Ethernet.h" con #include "EthernetLarge.h" nel tuo sketch. In alternativa, se, per qualche motivo, questa soluzione non funziona, puoi applicare la modifica manualmente utilizzando le istruzioni seguenti.
Estensione del buffer
Noto anche che per ottenere una buona stabilità probabilmente devi cambiare qualcos’altro.
In SSLClient.h devi cambiare questa riga.
unsigned char m_iobuf[2048];
in
unsigned char m_iobuf[BR_SSL_BUFSIZE_BIDI];
Modifica manuale
Innanzitutto, trova la posizione della libreria nella directory in cui è installato Arduino ( C:\Program Files (x86)\Arduino su Windows). All’interno di questa directory, vai a libraries\Ethernet\src ( C:\Program Files (x86)\Arduino\libraries\Ethernet\src su Windows). Modifica Ethernet.h per sostituire queste righe:
...
// Configure the maximum number of sockets to support. W5100 chips can have
// up to 4 sockets. W5200 & W5500 can have up to 8 sockets. Several bytes
// of RAM are used for each socket. Reducing the maximum can save RAM, but
// you are limited to fewer simultaneous connections.
#if defined(RAMEND) && defined(RAMSTART) && ((RAMEND - RAMSTART) <= 2048)
#define MAX_SOCK_NUM 4
#else
#define MAX_SOCK_NUM 8
#endif
// By default, each socket uses 2K buffers inside the Wiznet chip. If
// MAX_SOCK_NUM is set to fewer than the chip's maximum, uncommenting
// this will use larger buffers within the Wiznet chip. Large buffers
// can really help with UDP protocols like Artnet. In theory larger
// buffers should allow faster TCP over high-latency links, but this
// does not always seem to work in practice (maybe Wiznet bugs?)
//#define ETHERNET_LARGE_BUFFERS
...
Con queste:
...
// Configure the maximum number of sockets to support. W5100 chips can have
// up to 4 sockets. W5200 & W5500 can have up to 8 sockets. Several bytes
// of RAM are used for each socket. Reducing the maximum can save RAM, but
// you are limited to fewer simultaneous connections.
#define MAX_SOCK_NUM 2
// By default, each socket uses 2K buffers inside the Wiznet chip. If
// MAX_SOCK_NUM is set to fewer than the chip's maximum, uncommenting
// this will use larger buffers within the Wiznet chip. Large buffers
// can really help with UDP protocols like Artnet. In theory larger
// buffers should allow faster TCP over high-latency links, but this
// does not always seem to work in practice (maybe Wiznet bugs?)
#define ETHERNET_LARGE_BUFFERS
...
Potrebbe essere necessario utilizzare sudo o autorizzazioni da amministratore per apportare questa modifica. Cambiamo MAX_SOCK_NUMe ETHERNET_LARGE_BUFFERSquindi l’hardware Ethernet può allocare uno spazio maggiore per SSLClient. Tuttavia, uno svantaggio di questa modifica è che possiamo avere solo due socket contemporaneamente. Poiché la maggior parte dei microprocessori ha a malapena memoria sufficiente per una connessione SSL, questa limitazione si incontra raramente nella pratica.
Code
Ora proviamo a fare una semplice WebRequest con un client nativo.
Ma prima scriviamo il codice necessario per la connessione, proviamo a chiedere l’IP al server DHCP e, se fallisce, avviamo una connessione con un IP statico.
Inizializzare il dispositivo
Ethernet utilizza l’interfaccia SPI predefinita, quindi prima dobbiamo impostare il pin SS corretto (probabilmente non necessario).
// You can use Ethernet.init(pin) to configure the CS pin
//Ethernet.init(10); // Most Arduino shields
// Ethernet.init(5); // MKR ETH Shield
//Ethernet.init(0); // Teensy 2.0
//Ethernet.init(20); // Teensy++ 2.0
//Ethernet.init(15); // ESP8266 with Adafruit FeatherWing Ethernet
//Ethernet.init(33); // ESP32 with Adafruit FeatherWing Ethernet
// Ethernet.init(PA4); // STM32 with w5500
Ethernet.init(5); // Raspberry Pi Pico with w5500
Devi specificare anche un MAC address
// Enter a MAC address for your controller below.
// Newer Ethernet shields have a MAC address printed on a sticker on the shield
byte mac[] = { 0xDE, 0xAD, 0xBE, 0xEF, 0xFE, 0xED };
Quindi proviamo a fare una richiesta DHCP.
if (Ethernet.begin(mac)) { // Dynamic IP setup
Serial.println("DHCP OK!");
}
Ma se fallisce, proviamo a stabilire una connessione IP statica con questi parametri
// Set the static IP address to use if the DHCP fails to assign
#define MYIPADDR 192,168,1,28
#define MYIPMASK 255,255,255,0
#define MYDNS 192,168,1,1
#define MYGW 192,168,1,1
ed ecco il codice di connessione
Serial.println("Failed to configure Ethernet using DHCP");
// Check for Ethernet hardware present
if (Ethernet.hardwareStatus() == EthernetNoHardware) {
Serial.println(
"Ethernet shield was not found. Sorry, can't run without hardware. :(");
while (true) {
delay(1); // do nothing, no point running without Ethernet hardware
}
}
if (Ethernet.linkStatus() == LinkOFF) {
Serial.println("Ethernet cable is not connected.");
}
IPAddress ip(MYIPADDR);
IPAddress dns(MYDNS);
IPAddress gw(MYGW);
IPAddress sn(MYIPMASK);
Ethernet.begin(mac, ip, dns, gw, sn);
Serial.println("STATIC OK!");
Semplice richiesta HTTP
Prima di tutto, proveremo a fare una semplice richiesta HTTP. Ho scelto un servizio online creato per testare questo tipo di richiesta.
Userò un semplice servizio fornito da httpbin.org e puoi utilizzare la stessa API REST in HTTP e HTTPS .
Ricorda che HTTP funziona sulla porta 80 e HTTPS su 443, quindi devi convalidare un certificato per interrogare l’endpoint sulla porta 443.
Per stabilire la nostra connessione, utilizziamo l’EthernetClient di base.
// Initialize the Ethernet client library
// with the IP address and port of the server
// that you want to connect to (port 80 is default for HTTP):
EthernetClient client;
E poi, proviamo a connetterci e chiediamo un endpoint GET.
// if you get a connection, report back via serial:
if (client.connect(server, 80)) {
Serial.println("Connected!");
// Make a HTTP request:
client.println("GET /get HTTP/1.1");
client.println("Host: httpbin.org");
client.println("Connection: close");
client.println();
} else {
// if you didn't get a connection to the server:
Serial.println("connection failed");
}
Nel ciclo, attendiamo una risposta dal server.
// if there are incoming bytes available
// from the server, read them and print them:
int len = client.available();
E poi leggiamo la risposta e la inviamo alla seriale.
if (len > 0) {
byte buffer[80];
if (len > 80) len = 80;
client.read(buffer, len);
if (printWebData) {
Serial.write(buffer, len); // show in the serial monitor (slows some boards)
}
byteCount = byteCount + len;
}
// if the server's disconnected, stop the client:
if (!client.connected()) {
endMicros = micros();
Serial.println();
Serial.println("disconnecting.");
client.stop();
Serial.print("Received ");
Serial.print(byteCount);
Serial.print(" bytes in ");
float seconds = (float)(endMicros - beginMicros) / 1000000.0;
Serial.print(seconds, 4);
float rate = (float)byteCount / seconds / 1000.0;
Serial.print(", rate = ");
Serial.print(rate);
Serial.print(" kbytes/second");
Serial.println();
// do nothing forevermore:
while (true) {
delay(1);
}
}
E per finire, lo schizzo completo.
/*
Web client Raspberry Pi Pico (or other rp2040 boards)
and Arduino Ethernet library
This sketch connects to a test website (httpbin.org)
and try to do a GET request, the output is printed
on Serial
by Renzo Mischianti <www.mischianti.org>
https://www.mischianti.org
*/
#include <SPI.h>
#include <Ethernet.h>
// if you don't want to use DNS (and reduce your sketch size)
// use the numeric IP instead of the name for the server:
//IPAddress server(74,125,232,128); // numeric IP for Google (no DNS)
//char server[] = "www.google.com"; // name address for Google (using DNS)
char server[] = "httpbin.org"; // name address for Google (using DNS)
// Enter a MAC address for your controller below.
// Newer Ethernet shields have a MAC address printed on a sticker on the shield
byte mac[] = { 0xDE, 0xAD, 0xBE, 0xEF, 0xFE, 0xED };
// Set the static IP address to use if the DHCP fails to assign
#define MYIPADDR 192,168,1,28
#define MYIPMASK 255,255,255,0
#define MYDNS 192,168,1,1
#define MYGW 192,168,1,1
// Initialize the Ethernet client library
// with the IP address and port of the server
// that you want to connect to (port 80 is default for HTTP):
EthernetClient client;
// Variables to measure the speed
unsigned long beginMicros, endMicros;
unsigned long byteCount = 0;
bool printWebData = true; // set to false for better speed measurement
void setup() {
Serial.begin(115200);
while (!Serial) {delay(100);};
Serial.println("Begin Ethernet");
// You can use Ethernet.init(pin) to configure the CS pin
//Ethernet.init(10); // Most Arduino shields
// Ethernet.init(5); // MKR ETH Shield
//Ethernet.init(0); // Teensy 2.0
//Ethernet.init(20); // Teensy++ 2.0
//Ethernet.init(15); // ESP8266 with Adafruit FeatherWing Ethernet
//Ethernet.init(33); // ESP32 with Adafruit FeatherWing Ethernet
// Ethernet.init(PA4); // STM32 with w5500
Ethernet.init(17); // Raspberry Pi Pico with w5500
if (Ethernet.begin(mac)) { // Dynamic IP setup
Serial.println("DHCP OK!");
}else{
Serial.println("Failed to configure Ethernet using DHCP");
// Check for Ethernet hardware present
if (Ethernet.hardwareStatus() == EthernetNoHardware) {
Serial.println("Ethernet shield was not found. Sorry, can't run without hardware. :(");
while (true) {
delay(1); // do nothing, no point running without Ethernet hardware
}
}
if (Ethernet.linkStatus() == LinkOFF) {
Serial.println("Ethernet cable is not connected.");
}
IPAddress ip(MYIPADDR);
IPAddress dns(MYDNS);
IPAddress gw(MYGW);
IPAddress sn(MYIPMASK);
Ethernet.begin(mac, ip, dns, gw, sn);
Serial.println("STATIC OK!");
}
delay(5000);
Serial.print("Local IP : ");
Serial.println(Ethernet.localIP());
Serial.print("Subnet Mask : ");
Serial.println(Ethernet.subnetMask());
Serial.print("Gateway IP : ");
Serial.println(Ethernet.gatewayIP());
Serial.print("DNS Server : ");
Serial.println(Ethernet.dnsServerIP());
Serial.println("Ethernet Successfully Initialized");
// if you get a connection, report back via serial:
if (client.connect(server, 80)) {
Serial.println("Connected!");
// Make a HTTP request:
client.println("GET /get HTTP/1.1");
client.println("Host: httpbin.org");
client.println("Connection: close");
client.println();
} else {
// if you didn't get a connection to the server:
Serial.println("connection failed");
}
beginMicros = micros();
}
void loop() {
// if there are incoming bytes available
// from the server, read them and print them:
int len = client.available();
if (len > 0) {
byte buffer[80];
if (len > 80) len = 80;
client.read(buffer, len);
if (printWebData) {
Serial.write(buffer, len); // show in the serial monitor (slows some boards)
}
byteCount = byteCount + len;
}
// if the server's disconnected, stop the client:
if (!client.connected()) {
endMicros = micros();
Serial.println();
Serial.println("disconnecting.");
client.stop();
Serial.print("Received ");
Serial.print(byteCount);
Serial.print(" bytes in ");
float seconds = (float)(endMicros - beginMicros) / 1000000.0;
Serial.print(seconds, 4);
float rate = (float)byteCount / seconds / 1000.0;
Serial.print(", rate = ");
Serial.print(rate);
Serial.print(" kbytes/second");
Serial.println();
// do nothing forevermore:
while (true) {
delay(1);
}
}
}
Il risultato è questo.
Begin Ethernet
DHCP OK!
Local IP : 192.168.1.135
Subnet Mask : 255.255.255.0
Gateway IP : 192.168.1.1
DNS Server : 192.168.1.1
Ethernet Successfully Initialized
Connected!
HTTP/1.1 200 OK
Date: Fri, 16 Sep 2022 07:55:39 GMT
Content-Type: application/json
Content-Length: 198
Connection: close
Server: gunicorn/19.9.0
Access-Control-Allow-Origin: *
Access-Control-Allow-Credentials: true
{
"args": {},
"headers": {
"Host": "httpbin.org",
"X-Amzn-Trace-Id": "Root=1-63242bfb-38329e827b4986891d437152"
},
"origin": "82.53.128.115",
"url": "http://httpbin.org/get"
}
disconnecting.
Received 423 bytes in 0.1096, rate = 3.86 kbytes/second
Richiesta HTTPS
Ora, se cambiamo l’endpoint sulla porta 443, la richiesta sarà verso un server sicuro con crittografia SSL.
if (client.connect(server, 443)) {
Serial.println("Connected!");
// Make a HTTP request:
client.println("GET /get HTTP/1.1");
client.println("Host: httpbin.org");
client.println("Connection: close");
client.println();
} else {
// if you didn't get a connection to the server:
Serial.println("connection failed");
}
E otteniamo questa risposta.
Begin Ethernet
DHCP OK!
Local IP : 192.168.1.135
Subnet Mask : 255.255.255.0
Gateway IP : 192.168.1.1
DNS Server : 192.168.1.1
Ethernet Successfully Initialized
Connected!
HTTP/1.1 400 Bad Request
Server: awselb/2.0
Date: Fri, 16 Sep 2022 10:39:46 GMT
Content-Type: text/html
Content-Length: 220
Connection: close
<html>
<head><title>400 The plain HTTP request was sent to HTTPS port</title></head>
<body>
<center><h1>400 Bad Request</h1></center>
<center>The plain HTTP request was sent to HTTPS port</center>
</body>
</html>
disconnecting.
Received 370 bytes in 0.1078, rate = 3.43 kbytes/second
Quindi il problema è che i messaggi di richiesta e risposta non vengono trasmessi utilizzando SSL (Secure Sockets Layer) o il suo successore TLS (Transport Layer Security). Per aggiungere questa funzione, utilizzeremo SSLClient.
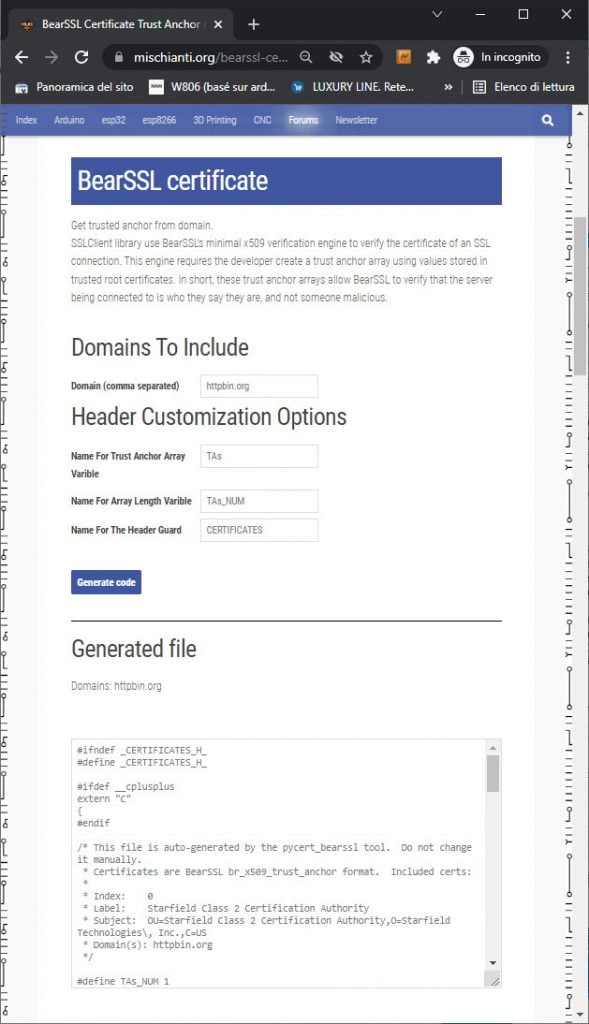
Recuperare il certificato
Per utilizzare una connessione SSL, abbiamo bisogno del certificato del server, ma in questo caso SSLClient utilizza un trucco fornito dall’implementazione di BearSSL. Un motore di verifica x509 minimo che consente l’utilizzo di Trust Anchors.
Aggiungo un semplice generatore online che puoi trovare qui .
Devi solo scrivere l’indirizzo del sito (httpbin.org) nella prima casella di input, fare clic su Generate code, copiare il codice e inserirlo in un file chiamato trust_anchors.h e metterlo nella cartella dello sketch.
Ecco il contenuto del trust_anchors.h.
#ifndef _CERTIFICATES_H_
#define _CERTIFICATES_H_
#ifdef __cplusplus
extern "C"
{
#endif
/* This file is auto-generated by the pycert_bearssl tool. Do not change it manually.
* Certificates are BearSSL br_x509_trust_anchor format. Included certs:
*
* Index: 0
* Label: Starfield Class 2 Certification Authority
* Subject: OU=Starfield Class 2 Certification Authority,O=Starfield Technologies\, Inc.,C=US
* Domain(s): httpbin.org
*/
#define TAs_NUM 1
static const unsigned char TA_DN0[] = {
0x30, 0x68, 0x31, 0x0b, 0x30, 0x09, 0x06, 0x03, 0x55, 0x04, 0x06, 0x13,
0x02, 0x55, 0x53, 0x31, 0x25, 0x30, 0x23, 0x06, 0x03, 0x55, 0x04, 0x0a,
0x13, 0x1c, 0x53, 0x74, 0x61, 0x72, 0x66, 0x69, 0x65, 0x6c, 0x64, 0x20,
0x54, 0x65, 0x63, 0x68, 0x6e, 0x6f, 0x6c, 0x6f, 0x67, 0x69, 0x65, 0x73,
0x2c, 0x20, 0x49, 0x6e, 0x63, 0x2e, 0x31, 0x32, 0x30, 0x30, 0x06, 0x03,
0x55, 0x04, 0x0b, 0x13, 0x29, 0x53, 0x74, 0x61, 0x72, 0x66, 0x69, 0x65,
0x6c, 0x64, 0x20, 0x43, 0x6c, 0x61, 0x73, 0x73, 0x20, 0x32, 0x20, 0x43,
0x65, 0x72, 0x74, 0x69, 0x66, 0x69, 0x63, 0x61, 0x74, 0x69, 0x6f, 0x6e,
0x20, 0x41, 0x75, 0x74, 0x68, 0x6f, 0x72, 0x69, 0x74, 0x79,
};
static const unsigned char TA_RSA_N0[] = {
0xb7, 0x32, 0xc8, 0xfe, 0xe9, 0x71, 0xa6, 0x04, 0x85, 0xad, 0x0c, 0x11,
0x64, 0xdf, 0xce, 0x4d, 0xef, 0xc8, 0x03, 0x18, 0x87, 0x3f, 0xa1, 0xab,
0xfb, 0x3c, 0xa6, 0x9f, 0xf0, 0xc3, 0xa1, 0xda, 0xd4, 0xd8, 0x6e, 0x2b,
0x53, 0x90, 0xfb, 0x24, 0xa4, 0x3e, 0x84, 0xf0, 0x9e, 0xe8, 0x5f, 0xec,
0xe5, 0x27, 0x44, 0xf5, 0x28, 0xa6, 0x3f, 0x7b, 0xde, 0xe0, 0x2a, 0xf0,
0xc8, 0xaf, 0x53, 0x2f, 0x9e, 0xca, 0x05, 0x01, 0x93, 0x1e, 0x8f, 0x66,
0x1c, 0x39, 0xa7, 0x4d, 0xfa, 0x5a, 0xb6, 0x73, 0x04, 0x25, 0x66, 0xeb,
0x77, 0x7f, 0xe7, 0x59, 0xc6, 0x4a, 0x99, 0x25, 0x14, 0x54, 0xeb, 0x26,
0xc7, 0xf3, 0x7f, 0x19, 0xd5, 0x30, 0x70, 0x8f, 0xaf, 0xb0, 0x46, 0x2a,
0xff, 0xad, 0xeb, 0x29, 0xed, 0xd7, 0x9f, 0xaa, 0x04, 0x87, 0xa3, 0xd4,
0xf9, 0x89, 0xa5, 0x34, 0x5f, 0xdb, 0x43, 0x91, 0x82, 0x36, 0xd9, 0x66,
0x3c, 0xb1, 0xb8, 0xb9, 0x82, 0xfd, 0x9c, 0x3a, 0x3e, 0x10, 0xc8, 0x3b,
0xef, 0x06, 0x65, 0x66, 0x7a, 0x9b, 0x19, 0x18, 0x3d, 0xff, 0x71, 0x51,
0x3c, 0x30, 0x2e, 0x5f, 0xbe, 0x3d, 0x77, 0x73, 0xb2, 0x5d, 0x06, 0x6c,
0xc3, 0x23, 0x56, 0x9a, 0x2b, 0x85, 0x26, 0x92, 0x1c, 0xa7, 0x02, 0xb3,
0xe4, 0x3f, 0x0d, 0xaf, 0x08, 0x79, 0x82, 0xb8, 0x36, 0x3d, 0xea, 0x9c,
0xd3, 0x35, 0xb3, 0xbc, 0x69, 0xca, 0xf5, 0xcc, 0x9d, 0xe8, 0xfd, 0x64,
0x8d, 0x17, 0x80, 0x33, 0x6e, 0x5e, 0x4a, 0x5d, 0x99, 0xc9, 0x1e, 0x87,
0xb4, 0x9d, 0x1a, 0xc0, 0xd5, 0x6e, 0x13, 0x35, 0x23, 0x5e, 0xdf, 0x9b,
0x5f, 0x3d, 0xef, 0xd6, 0xf7, 0x76, 0xc2, 0xea, 0x3e, 0xbb, 0x78, 0x0d,
0x1c, 0x42, 0x67, 0x6b, 0x04, 0xd8, 0xf8, 0xd6, 0xda, 0x6f, 0x8b, 0xf2,
0x44, 0xa0, 0x01, 0xab,
};
static const unsigned char TA_RSA_E0[] = {
0x03,
};
static const br_x509_trust_anchor TAs[] = {
{
{ (unsigned char *)TA_DN0, sizeof TA_DN0 },
BR_X509_TA_CA,
{
BR_KEYTYPE_RSA,
{ .rsa = {
(unsigned char *)TA_RSA_N0, sizeof TA_RSA_N0,
(unsigned char *)TA_RSA_E0, sizeof TA_RSA_E0,
} }
}
},
};
#ifdef __cplusplus
} /* extern "C" */
#endif
#endif /* ifndef _CERTIFICATES_H_ */
Aggiungere il wrapper SSLClient
Codice
Ora aggiungeremo la libreria SSLClient e il file trust_anchors.h.
#include <SPI.h>
#include <EthernetLarge.h>
#include <SSLClient.h>
#include "trust_anchors.h"
Ho anche cambiato la libreria Ethernet con EthernetLarge invece della modifica descritta nella sezione sopra.
Quindi applica il wrapper EthernetClient con tutti i riferimenti di Trust Anchors. Il file contiene nomi di array di trust anchor generati TAs con lunghezza TAs_NUM.
// Choose the analog pin to get semi-random data from for SSL
// Pick a pin that's not connected or attached to a randomish voltage source
const int rand_pin = A5;
// Initialize the SSL client library
// We input an EthernetClient, our trust anchors, and the analog pin
EthernetClient base_client;
SSLClient client(base_client, TAs, (size_t)TAs_NUM, rand_pin);
E cambiamo la porta in 443 (HTTPS).
// if you get a connection, report back via serial:
if (client.connect(server, 443)) {
Serial.print("connected to ");
// Make a HTTP request:
client.println("GET /get HTTP/1.1");
client.println("Host: httpbin.org");
client.println("Connection: close");
client.println();
} else {
// if you didn't get a connection to the server:
Serial.println("connection failed");
}
Ecco lo sketch completo.
/*
Web SSL client Raspberry Pi Pico and rp2040 boards
and Arduino EthernetLarge library
This sketch connects to a test website (httpbin.org)
and try to do a secure GET request on port 443,
to do the SSL request we use SSLClient with the
site Trust Anchor
the output is printed on Serial
by Renzo Mischianti <www.mischianti.org>
https://www.mischianti.org
*/
#include <SPI.h>
#include <EthernetLarge.h>
#include <SSLClient.h>
#include "trust_anchors.h"
// Enter a MAC address for your controller below.
// Newer Ethernet shields have a MAC address printed on a sticker on the shield
byte mac[] = { 0xDE, 0xAD, 0xBE, 0xEF, 0xFE, 0xED };
// if you don't want to use DNS (and reduce your sketch size)
// use the numeric IP instead of the name for the server:
//IPAddress server(74,125,232,128); // numeric IP for Google (no DNS)
//char server[] = "www.google.com"; // name address for Google (using DNS)
char server[] = "httpbin.org"; // name address for Google (using DNS)
// Set the static IP address to use if the DHCP fails to assign
#define MYIPADDR 192,168,1,28
#define MYIPMASK 255,255,255,0
#define MYDNS 192,168,1,1
#define MYGW 192,168,1,1
// Choose the analog pin to get semi-random data from for SSL
// Pick a pin that's not connected or attached to a randomish voltage source
const int rand_pin = A0;
// Initialize the SSL client library
// We input an EthernetClient, our trust anchors, and the analog pin
EthernetClient base_client;
SSLClient client(base_client, TAs, (size_t)TAs_NUM, rand_pin);
// Variables to measure the speed
unsigned long beginMicros, endMicros;
unsigned long byteCount = 0;
bool printWebData = true; // set to false for better speed measurement
void setup() {
Serial.begin(115200);
while (!Serial) {delay(100);};
Serial.println("Begin Ethernet");
// You can use Ethernet.init(pin) to configure the CS pin
//Ethernet.init(10); // Most Arduino shields
// Ethernet.init(5); // MKR ETH Shield
//Ethernet.init(0); // Teensy 2.0
//Ethernet.init(20); // Teensy++ 2.0
//Ethernet.init(15); // ESP8266 with Adafruit FeatherWing Ethernet
//Ethernet.init(33); // ESP32 with Adafruit FeatherWing Ethernet
// Ethernet.init(PA4); // STM32 with w5500
Ethernet.init(17); // Raspberry Pi Pico with w5500
if (Ethernet.begin(mac)) { // Dynamic IP setup
Serial.println("DHCP OK!");
}else{
Serial.println("Failed to configure Ethernet using DHCP");
// Check for Ethernet hardware present
if (Ethernet.hardwareStatus() == EthernetNoHardware) {
Serial.println("Ethernet shield was not found. Sorry, can't run without hardware. :(");
while (true) {
delay(1); // do nothing, no point running without Ethernet hardware
}
}
if (Ethernet.linkStatus() == LinkOFF) {
Serial.println("Ethernet cable is not connected.");
}
IPAddress ip(MYIPADDR);
IPAddress dns(MYDNS);
IPAddress gw(MYGW);
IPAddress sn(MYIPMASK);
Ethernet.begin(mac, ip, dns, gw, sn);
Serial.println("STATIC OK!");
}
delay(5000);
Serial.print("Local IP : ");
Serial.println(Ethernet.localIP());
Serial.print("Subnet Mask : ");
Serial.println(Ethernet.subnetMask());
Serial.print("Gateway IP : ");
Serial.println(Ethernet.gatewayIP());
Serial.print("DNS Server : ");
Serial.println(Ethernet.dnsServerIP());
Serial.println("Ethernet Successfully Initialized");
// if you get a connection, report back via serial:
if (client.connect(server, 443)) {
Serial.print("connected to ");
// Make a HTTP request:
client.println("GET /get HTTP/1.1");
client.println("Host: httpbin.org");
client.println("Connection: close");
client.println();
} else {
// if you didn't get a connection to the server:
Serial.println("connection failed");
}
beginMicros = micros();
}
void loop() {
// if there are incoming bytes available
// from the server, read them and print them:
int len = client.available();
if (len > 0) {
byte buffer[80];
if (len > 80) len = 80;
client.read(buffer, len);
if (printWebData) {
Serial.write(buffer, len); // show in the serial monitor (slows some boards)
}
byteCount = byteCount + len;
}
// if the server's disconnected, stop the client:
if (!client.connected()) {
endMicros = micros();
Serial.println();
Serial.println("disconnecting.");
client.stop();
Serial.print("Received ");
Serial.print(byteCount);
Serial.print(" bytes in ");
float seconds = (float)(endMicros - beginMicros) / 1000000.0;
Serial.print(seconds, 4);
float rate = (float)byteCount / seconds / 1000.0;
Serial.print(", rate = ");
Serial.print(rate);
Serial.print(" kbytes/second");
Serial.println();
// do nothing forevermore:
while (true) {
delay(1);
}
}
}
Ora, quando eseguiamo lo schizzo, otteniamo questo output.
Begin Ethernet
DHCP OK!
Local IP : 192.168.1.135
Subnet Mask : 255.255.255.0
Gateway IP : 192.168.1.1
DNS Server : 192.168.1.1
Ethernet Successfully Initialized
connected to HTTP/1.1 200 OK
Date: Fri, 16 Sep 2022 10:57:24 GMT
Content-Type: application/json
Content-Length: 199
Connection: close
Server: gunicorn/19.9.0
Access-Control-Allow-Origin: *
Access-Control-Allow-Credentials: true
{
"args": {},
"headers": {
"Host": "httpbin.org",
"X-Amzn-Trace-Id": "Root=1-63245694-23b9f2546222ba04034ff19e"
},
"origin": "82.53.128.115",
"url": "https://httpbin.org/get"
}
disconnecting.
Received 424 bytes in 0.2244, rate = 1.89 kbytes/second
Grazie
Uso questa libreria SSLClient nella mia libreria EMailSender per utilizzare il server SMTP (SSL) di Gmail con Ethernet. Sfortunatamente, le connessioni SSL richiedono molte risorse, ma Arduino SAMD, STM32, rp2040 ed ESP32 le hanno.
- Schede Raspberry Pi Pico e rp2040: pinout, specifiche e configurazione IDE Arduino
- Schede Raspberry Pi Pico e rp2040: filesystem LittleFS integrato
- Scheda Raspberry Pi Pico e rp2040: ethernet w5500 e requests HTTP e HTTPS (SSL)
- Schede Raspberry Pi Pico e rp2040: WiFiNINA con coprocessore WiFi ESP32
- Schede Raspberry Pi Pico e rp2040: come utilizzare una scheda SD
- Dallas ds18b20
- Collegamento dell’EByte E70 ai dispositivi Raspberry Pi Pico (rp2040) ed un semplice sketch di esempio