Wireless Sensors: The Future of Connectivity Today (WiFi, LoRa, ZigBee, Bluetooth and RF)
In this digital age, connectivity has become a vital aspect of our lives. From smartphones to smart homes, we are constantly surrounded by devices that rely on internet connectivity. However, the future of connectivity goes beyond the scope of traditional networks. Enter wireless sensor nodes, the next big thing in the world of connectivity.

Wireless sensor nodes are small, battery-powered devices that can gather, process, and transmit data wirelessly. These nodes have the potential to revolutionize various industries, from healthcare to agriculture. By placing these nodes in the field, researchers and businesses can collect real-time data and gain valuable insights into their operations.
Imagine a world where farmers can monitor soil moisture levels and automatically water their crops, or hospitals can track the vital signs of patients remotely, ensuring timely care. This is the promise of wireless sensor nodes.
With advancements in technology, these nodes have become smaller, more energy-efficient, and cost-effective. They can communicate with each other and form networks, creating a seamless web of connectivity. The possibilities are endless.
In this article, we will explore the wonders of wireless sensor nodes and how they are shaping the future of connectivity. Prepare to be amazed by the potential of these tiny devices.
Importance and applications of wireless sensor nodes
Wireless sensor nodes are integral components of modern data collection and monitoring systems. Their ability to operate independently while transmitting critical information makes them essential in various sectors. One of the most significant applications of these nodes is in environmental monitoring. With the increasing threat of climate change, organizations are using sensor nodes to collect data on air quality, temperature, humidity, and other environmental factors. This real-time data helps scientists and policymakers make informed decisions to mitigate the effects of climate change.
In agriculture, wireless sensor nodes have transformed traditional farming practices. These devices allow farmers to monitor soil conditions, crop health, and weather patterns remotely. For instance, soil moisture sensors can provide precise data on when to irrigate, reducing water waste and optimizing crop yields. Additionally, farmers can utilize pest detection nodes to monitor insect activity, enabling them to apply pesticides only when necessary. This not only boosts productivity but also supports sustainable farming practices.

Healthcare is another field that has benefited immensely from wireless sensor nodes. These devices can monitor patient vital signs and transmit the data to healthcare providers in real time. This capability is particularly useful for remote patient monitoring, where patients can be cared for from the comfort of their homes. Wireless sensors can track parameters such as heart rate, blood pressure, and glucose levels, allowing for timely interventions. This technology enhances patient care while reducing the burden on healthcare facilities.
Advantages of wireless sensor nodes
The advantages of wireless sensor nodes are numerous and varied, contributing to their growing adoption across multiple industries. One of the primary benefits is their ability to facilitate real-time data collection and analysis. This instant access to information allows businesses and organizations to make informed decisions quickly, improving responsiveness and operational efficiency. Additionally, the ability to gather data without the need for extensive wiring or infrastructure significantly reduces installation costs and complexity.
Energy efficiency is another significant advantage of wireless sensor nodes. Many of these devices are designed to consume minimal power, allowing them to operate for extended periods on battery power. Innovations such as energy harvesting technologies enable them to recharge from their environment, further extending their operational lifespan. This feature is particularly beneficial in remote or hard-to-reach locations where traditional power sources are unavailable, making wireless sensor nodes a practical solution for a wide range of applications.
Moreover, wireless sensor nodes are highly scalable, allowing organizations to expand their networks as needed without significant additional investment. This flexibility enables businesses to start small and gradually increase their data collection capabilities as their needs evolve. The modular nature of these systems means that adding more nodes can enhance data granularity and coverage, leading to more comprehensive insights and improved decision-making.
Compare advantages of LoRa, RF, ZigBee, Bluetooth and WiFi
Wireless sensor nodes can communicate using various technologies, including LoRa, RF (Radio Frequency), ZigBee, Bluetooth, and Wi-Fi. Each of these communication methods has distinct advantages depending on the application. Here’s a breakdown of their differences and advantages:
LoRa (Long Range)
LoRa is a long-range, low-power wireless communication technology, particularly designed for IoT (Internet of Things) applications.
- Advantages:
- Long Range: LoRa can communicate over several kilometers, making it ideal for rural areas or applications requiring wide-area coverage.
- Low Power Consumption: Designed for low power, making it suitable for battery-powered sensor nodes that need to last for months or even years without battery replacement.
- Scalability: Supports many devices in a network, which is ideal for large IoT deployments.
- Penetration: Good building penetration, making it effective for urban environments.
- Cost: Low cost for both devices and deployment, with no need for complex infrastructure like cellular networks.
- Use Cases: Smart agriculture, smart cities, industrial IoT, remote monitoring.
RF (Radio Frequency)
RF communication covers a broad spectrum and typically refers to short-range wireless technologies like those using 433 MHz, 868 MHz, or 2.4 GHz bands.
- Advantages:
- Flexibility: RF modules can be designed for a wide range of frequencies, allowing customization based on specific application needs.
- Low Power: Like LoRa, RF communication can also be optimized for low-power consumption, making it suitable for battery-powered sensor nodes.
- Cost: RF modules are generally inexpensive, especially in simple systems where sophisticated protocols (like those used in Wi-Fi) are not required.
- Simplicity: RF-based systems can be easier to deploy and manage, especially for small or localized networks.
- Range: Typically offers shorter ranges than LoRa, but is sufficient for applications like home automation or industrial control in smaller areas.
- Use Cases: Home automation, short-range industrial monitoring, low-cost communication.
Zigbee
Zigbee is a wireless standard based on IEEE 802.15.4, specifically designed for low-power, low-data-rate applications, making it ideal for wireless sensor networks and the Internet of Things.
- Advantages:
- Mesh Networking: Allows nodes to communicate with each other to extend the network’s range, ensuring greater reliability.
- Low Power Consumption: Excellent for battery-powered devices, offering long operational life.
- Standardization: Ensures interoperability between products from different vendors.
- Cost: Provides cost-effective solutions for large-scale deployment.
- Security: Includes robust security mechanisms, including AES-128 encryption.
- Use Cases: Smart homes (lighting, thermostats), industrial automation, agricultural monitoring, smart cities.
Bluetooth
Bluetooth is a short-range wireless communication standard, ubiquitous in billions of devices, from phones to accessories. For sensor applications, its Bluetooth Low Energy (BLE) variant is the most important, as it is optimized for extremely low power consumption and for transmitting small amounts of data.
- Advantages:
- Ubiquity and Native Support: Integrated into nearly every smartphone, tablet, and PC, it allows for a direct connection without the need for additional gateways.
- Extremely Low Power Consumption (BLE): Designed to operate for months or even years on a single coin cell battery, making it ideal for autonomous sensors.
- Low Cost: The huge production volume for the consumer market has made Bluetooth modules extremely inexpensive.
- Ease of Use: Pairing and managing connections are simple and familiar to the end-user, easing adoption.
- Use Cases: Wearables (fitness trackers, smartwatches), medical sensors, home automation (beacons, smart locks), proximity tracking (asset tracking), consumer electronics.
Wi-Fi
Wi-Fi is a high-speed wireless networking technology commonly used for local area networks (LANs), allowing sensor nodes to communicate over existing internet infrastructure.
- Advantages:
- High Data Rates: Wi-Fi can support much higher data rates compared to LoRa and most RF systems, making it suitable for applications requiring the transmission of large data volumes.
- Network Infrastructure: Wi-Fi networks are widely available, especially in urban areas, reducing the need for dedicated infrastructure.
- Integration with IP Networks: Since Wi-Fi uses the same protocols as the internet, it’s easier to integrate sensor nodes into cloud-based systems for real-time monitoring and data analytics.
- Bi-directional Communication: Wi-Fi allows for high-capacity bi-directional communication, which is useful in interactive applications or when firmware updates are needed.
- Use Cases: Smart homes, real-time video monitoring, data-heavy applications, localized sensor networks.
Summary of Key Differences
| Feature | LoRa | RF | Wi-Fi | Zigbee | Bluetooth |
| Range | Long-range (up to 10+ km) | Short to medium range (a few km) | Short range (up to 100-200 meters) | Medium (10-100m, extended with mesh) | Short (up to 100m, depending on version) |
| Power Consumption | Very low | Low | High | Low | Very low (especially BLE) |
| Data Rate | Low (suitable for small data) | Low to moderate | High (suitable for large data) | Low to moderate (250 kbps) | Moderate (up to 2 Mbps for BLE) |
| Cost | Low | Low | Higher | Low | Low |
| Infrastructure Needed | Minimal (LoRa gateways) | Minimal (simple RF modules) | High (Wi-Fi routers/access points) | Moderate (coordinators, routers) | Minimal (direct connection to gateway/smartphone) |
| Network Capacity | High (supports many nodes) | Medium | Low to medium | High (thousands of nodes in a mesh network) | Low (few devices per master) |
Each technology excels in different contexts, so the choice depends on factors like range, power consumption, data needs, and existing infrastructure.
Challenges and limitations of wireless sensor nodes
Despite the many advantages of wireless sensor nodes, several challenges and limitations must be addressed for widespread adoption. One of the primary concerns is the issue of connectivity. In areas with weak signal strength or high interference, the reliability of data transmission can be compromised. This unreliability can result in data loss or delays, which can significantly impact decision-making processes. Organizations need to implement robust networks to ensure that sensor nodes can communicate effectively under various conditions.
Another challenge is the potential for battery life limitations. Although many wireless sensor nodes are designed for energy efficiency, their battery life can be affected by factors such as environmental conditions and transmission frequency. In applications where continuous data transmission is required, the need for frequent battery replacements can be a logistical burden. Researchers are exploring advanced energy solutions, including energy harvesting technologies, to mitigate this issue, but it remains a concern.
Security is also a significant limitation. Wireless sensor nodes are vulnerable to cyber-attacks, which can compromise the integrity of the data they collect. Given the sensitive nature of the information gathered—especially in healthcare and environmental monitoring—ensuring robust security measures is paramount. Organizations must implement encryption, secure authentication protocols, and regular software updates to safeguard their networks from potential threats.
Current trends and advancements in wireless sensor nodes
The landscape of wireless sensor nodes is continually evolving, driven by rapid technological advancements. One of the most notable trends is the increasing miniaturization of these devices. Modern sensor nodes are becoming smaller and more compact, allowing for easier integration into various applications. This miniaturization not only makes them less intrusive but also enables their deployment in previously inaccessible areas, such as remote monitoring of wildlife or environmental conditions in challenging terrains.
Another significant trend is the integration of artificial intelligence (AI) and machine learning (ML) into wireless sensor networks. These technologies enhance data processing capabilities by enabling predictive analytics and automated decision-making. For instance, AI algorithms can analyze the data collected by sensor nodes to predict equipment failures in industrial settings, allowing for proactive maintenance. This integration leads to more efficient operations and reduced downtime, ultimately saving costs.
Here a selection of e70 E70 433/915 T S/S2 - E70 433/915 MT S
Furthermore, the development of low-power wide-area networks (LPWAN) is revolutionizing the connectivity options for wireless sensor nodes. LPWAN technologies, such as LoRaWAN and Sigfox, enable long-range communication while consuming minimal power. This advancement allows sensor nodes to transmit data over significant distances without the need for frequent battery replacements. As these networks become more widespread, the potential applications for wireless sensor nodes will expand, particularly in smart cities and large-scale agricultural projects.
Consideration About the Owner of LoRaWAN (Semtech)
LoRaWAN technology is largely controlled and promoted by Semtech Corporation, the company that owns the intellectual property (IP) behind LoRa. Semtech plays a central role in advancing and standardizing LoRaWAN, while collaborating with organizations like the LoRa Alliance, which is a collective of companies pushing for global adoption of the LoRaWAN standard.
Positive Aspects of Semtech’s Role
- Innovation and Standardization: Semtech has played a critical role in bringing LoRa to the forefront of IoT communication. By maintaining ownership of the core IP and actively working with the LoRa Alliance, they have established a robust standard for low-power, long-range communication.
- Global Adoption: Through Semtech’s efforts, LoRaWAN has been adopted globally, with a growing ecosystem of manufacturers, developers, and service providers.
- Open Ecosystem: Although Semtech controls the LoRa physical layer, the LoRaWAN protocol is open, allowing companies to innovate on top of the technology, fostering a vibrant IoT ecosystem.
Challenges with Ownership
- Monopoly on Key Technology: Since Semtech owns the core LoRa technology, it essentially maintains a monopoly on the production of LoRa chips. This can create challenges for innovation or competition, as any advancements still need to go through Semtech’s ecosystem.
- Cost Structure: With a single company controlling the core IP, pricing of the underlying hardware (chips, transceivers) is controlled by Semtech. While the prices are relatively low for IoT applications, the lack of competition could mean limited downward pressure on prices in the future.
- Slow Evolution: Since the core technology is owned by one company, the pace of innovation and improvement might be slower than in fully open-source technologies or competitive markets. Semtech’s control over the LoRa ecosystem can dictate the speed and direction of its evolution.
In my opinion, if you don’t need a particular need like creating a global network in zero time, It’s preferable to create an MQTT server and a simple gateway.
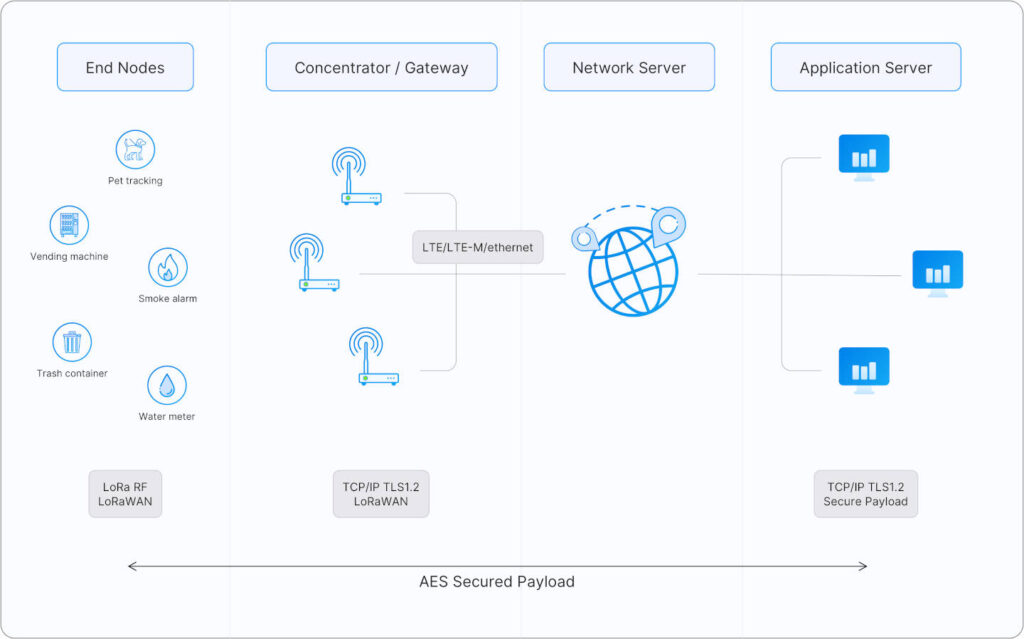
The role of wireless sensor nodes in the Internet of Things (IoT)
Wireless sensor nodes are pivotal to the growth and functionality of the Internet of Things (IoT). They serve as the foundational building blocks that enable devices to communicate and share data seamlessly. By embedding these nodes into everyday objects, from home appliances to industrial machinery, the IoT ecosystem can collect vast amounts of data from the physical world. This data is then analyzed and utilized to create smarter, more efficient systems that enhance our daily lives.
In smart homes, for example, wireless sensor nodes can monitor various environmental conditions, such as temperature, humidity, and light levels. These nodes can interact with other smart devices, such as thermostats and lights, to optimize energy consumption. Homeowners can receive alerts and control their devices remotely through mobile applications, leading to increased comfort and energy savings. The integration of sensor nodes in smart homes exemplifies how the IoT can transform traditional living spaces into intelligent environments.
In industrial applications, wireless sensor nodes facilitate predictive maintenance by monitoring equipment performance in real time. They can detect anomalies in machinery and alert operators before failures occur. This proactive approach minimizes downtime and significantly reduces maintenance costs. Moreover, industries can leverage the data collected by these sensors to optimize production processes, improve supply chain management, and enhance overall operational efficiency.
Case studies showcasing the use of wireless sensor nodes
Numerous case studies illustrate the transformative impact of wireless sensor nodes across various industries. One compelling example comes from the agricultural sector. A farm in California implemented a network of wireless sensor nodes to monitor soil moisture levels across its fields. By gathering real-time data, the farmers could optimize their irrigation schedules, resulting in a 30% reduction in water consumption while maintaining crop yield. The success of this initiative not only highlighted the benefits of efficient resource use but also served as a model for sustainable farming practices.
In the healthcare domain, a hospital in New York employed wireless sensor nodes to monitor patients with chronic illnesses remotely. By equipping patients with wearable sensors that tracked vital signs, healthcare providers could receive immediate alerts about any concerning changes in their health. This proactive monitoring approach led to improved patient outcomes, as medical staff could intervene sooner when necessary. The case study underscores the potential of wireless sensor nodes to enhance patient care while relieving pressure on hospital resources.
Another noteworthy case study involves environmental monitoring in urban areas. A city in Europe deployed a network of wireless sensor nodes throughout its parks and public spaces to monitor air quality and noise levels. The data collected enabled city officials to identify pollution hotspots and develop targeted interventions to improve overall air quality. This initiative not only enhanced public health but also contributed to the city’s sustainability goals. Such examples showcase the versatility of wireless sensor nodes in addressing real-world challenges and improving quality of life.
Security considerations for wireless sensor nodes
As wireless sensor nodes become more prevalent, ensuring their security is critical. These devices are often deployed in vulnerable locations, making them susceptible to physical tampering and cyber threats. One of the primary security concerns is the potential for data interception during transmission. If an attacker gains access to the data being transmitted, sensitive information can be compromised. Implementing robust encryption methods is essential to protect data integrity and confidentiality.
Additionally, secure authentication protocols must be established to regulate access to the network. Unauthorized access can lead to manipulation of the sensor nodes, resulting in false data being reported. Organizations should adopt best practices for device authentication, ensuring that only trusted devices can communicate within the network. Regular software updates and patches are also crucial to address any vulnerabilities that may arise over time.
Another important aspect of security is physical protection. Since many wireless sensor nodes are deployed in remote or public areas, they may be at risk of theft or vandalism. Employing protective casing or secure mounting solutions can help safeguard these devices against physical damage. Furthermore, organizations should conduct regular audits and risk assessments to identify potential security weaknesses and implement corrective measures proactively.
EByte solution
As you can see in my site I write a lot of library about EByte LoRa device, these series of devices use an hardware closed security implementation. As you can understand It’s quite secure but I think that not exist an environment completely secure.

Here’s an overview of the security mechanisms in EByte‘s E32, E22, and E220 modules
| Feature | E32 | E22 | E220 |
|---|---|---|---|
| Chip | sx1276-sx1278 | sx1262-sx1268 | LLCC68 |
| Range | 3Km – 8Km | 5km – 11km | 5Km – 10Km |
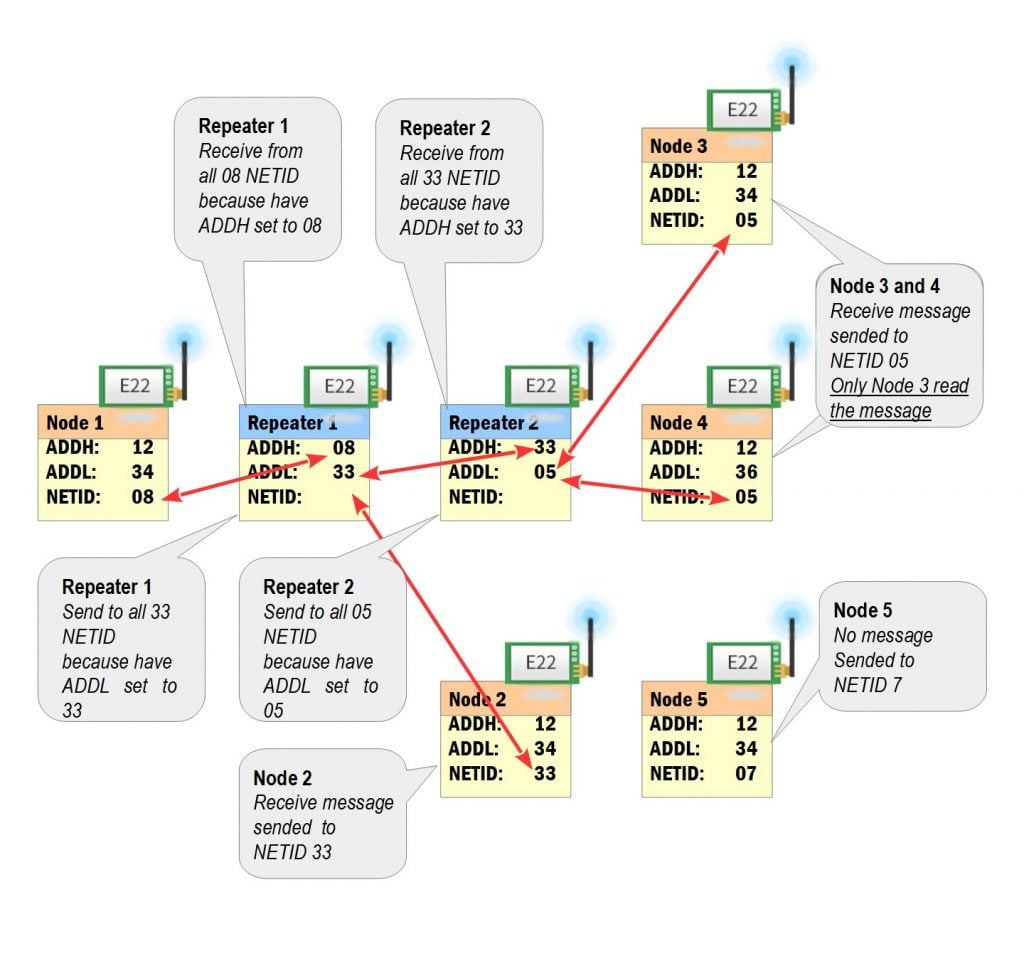
| Repeater | No repeater | Repeater | No repeater |
| Remote Config | No | Yes | No |
| Power Consumption | Best | Good | Very Good |
| Sleep Consumption | Sleep 4μA | Sleep 496μA | Sleep 6μA |
| Transmission & Receiving Power | Similar power consumption | Similar power consumption | Similar power consumption |
| Message Size (bytes) | 58 | 240 | 200 |
| Buffer Size (bytes) | 512 (ok) | 1000 (good) | 400 (why?????) |
| Max Air Data Rate (bps) | 19.2k | 62.5k | 62.5k |
| Encryption | One standard | Configurable | Configurable crypt |
| Price | Less expensive | More expensive | Less expensive |
Here a selection of e32 AliExpress (433MHz 5Km) - AliExpress (433MHz 8Km) - AliExpress (433MHz 16Km) - AliExpress (868MHz 915MHz 5.5Km) - AliExpress (868MHz 915MHz 8Km)
Here a selection of e22 AliExpress (433MHz 5.5Km) - AliExpress (433MHz 10Km) - AliExpress (868MHz 915Mhz 5.5Km) - AliExpress (868MHz 915Mhz 10Km)
Here a selection of e220 E220-400T22D 433MHz 5Km - E220-400T30D 433MHz 10Km - E220-900T22D 868MHz 915MHz 5Km - E220-900T30D 868MHz 915MHz 10Km
AES Encryption
The primary security mechanism in EByte modules, including the E32, E22, and E220, is AES (Advanced Encryption Standard) encryption. AES is a well-known and robust encryption algorithm that ensures that data transmitted between modules remains confidential and protected from unauthorized access.
- Encryption Level: The AES algorithm used is typically 128-bit, which provides a high level of security for most industrial and IoT applications. AES-128 is widely considered secure enough for most scenarios unless there is a need for exceptionally high levels of security (e.g., in military or government use cases).
- Data Security: When enabled, AES encryption ensures that data transmitted over the air is unreadable by any third parties, securing communications from eavesdropping.
However, it’s important for developers to properly configure and manage the encryption keys. Poor key management practices, like reusing keys across multiple devices or failing to change them regularly, could expose systems to attacks.
Frequency Hopping (FHSS)
Some EByte modules, such as the E22 and E220, support frequency hopping spread spectrum (FHSS). This is an additional layer of security that works by changing the frequency of communication at predetermined intervals, making it harder for potential attackers to intercept or jam the signal.
- Security Benefits: FHSS reduces the likelihood of successful interception because the signal is not broadcast on a single, fixed frequency. It also helps to mitigate jamming attacks, where an adversary attempts to disrupt communication by flooding a specific frequency with noise.
FHSS can enhance both the security and the reliability of communication, especially in environments where multiple wireless systems operate in the same frequency band.
Data Integrity and Error Correction
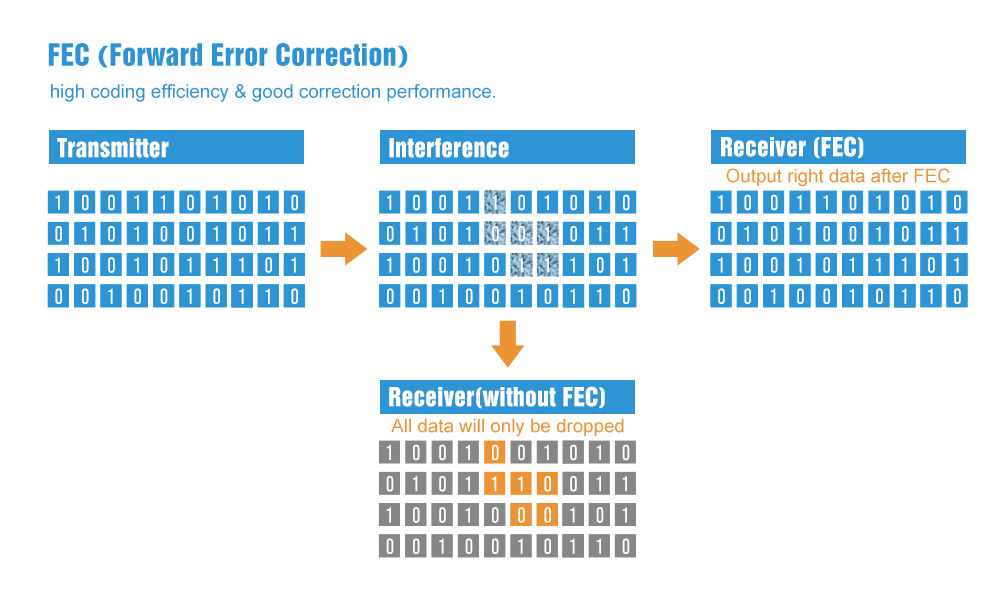
EByte modules like E32, E22, and E220 incorporate error correction mechanisms, such as forward error correction (FEC), which not only improves communication reliability but also enhances security.
- Error Detection and Correction: By detecting and correcting errors in the transmitted data, FEC ensures that the data received matches the data sent. This minimizes the risk of data tampering during transmission and protects against packet corruption, whether due to interference or deliberate attacks.
- Security Implication: This helps prevent attacks such as data injection, where an attacker might try to introduce malicious data into the communication stream.
Access Control via Unique IDs and Addressing
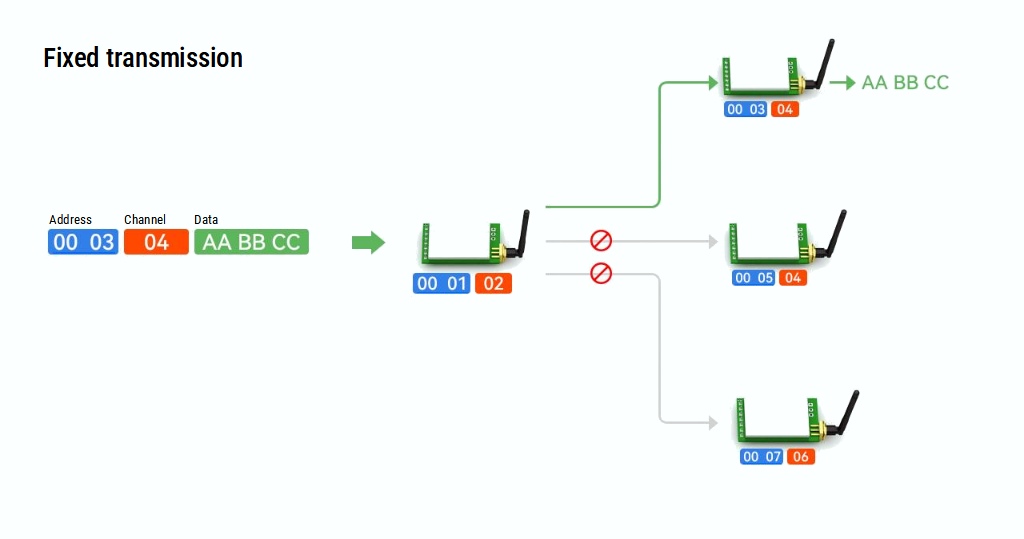
EByte modules often use unique device IDs or addressing schemes to control access to the communication channel. Each device can be assigned a specific ID, and communication is only allowed between authorized devices, adding a layer of access control.
- Network Access Control: This prevents unauthorized devices from joining the network or participating in communication. Only devices with the correct IDs or addresses will be able to send or receive data.
- Security Benefit: While this doesn’t replace encryption, it adds an additional barrier, especially when used in conjunction with AES encryption and other security measures.
Proprietary Protocols and Custom Configurations
While EByte provides general support for LoRa technology, some modules like the E32, E22, and E220 can be configured to use proprietary communication protocols that EByte has developed. Proprietary protocols can offer additional security by making it harder for attackers to understand the data structure and communication mechanisms, thus increasing the difficulty of hacking the system.
- Custom Frequency Bands and Transmission Modes: EByte modules are highly configurable, allowing developers to set custom frequency bands, data rates, and transmission modes. This flexibility enables the deployment of non-standard configurations that are less likely to be targeted by general-purpose attacks.
Limitations and Best Practices
While EByte modules offer several security features, the overall security of a system depends on how these features are implemented. Some potential limitations and best practices include:
- Key Management: AES encryption is only as strong as the management of the encryption keys. It’s crucial to regularly change keys and ensure they are securely distributed and stored.
- Physical Security: Since these modules are typically used in IoT devices, ensuring physical security is essential. Unauthorized physical access to the devices could compromise the entire system.
- Firmware Updates: EByte devices rely on firmware, so it’s important to ensure that devices are running the latest, most secure firmware versions. Regular updates can patch vulnerabilities that may arise over time.
Future prospects and potential developments in wireless sensor nodes
The future of wireless sensor nodes is bright, with numerous advancements on the horizon. One promising area of development is the integration of advanced materials and nanotechnology. Researchers are exploring the use of flexible and stretchable materials to create more adaptable sensor nodes that can be embedded in various environments. This innovation could lead to new applications in wearable technology, smart textiles, and even biomedical devices, expanding the capabilities of wireless sensor nodes.
Another exciting prospect is the continuous improvement in energy harvesting technologies. As the demand for sustainable solutions grows, researchers are focusing on developing sensor nodes that can harvest energy from their surroundings, such as solar, thermal, or kinetic energy. This advancement would reduce the reliance on batteries, making these devices even more viable for long-term deployment in remote areas. Such innovations would enable wireless sensor nodes to operate indefinitely, significantly increasing their utility across various applications.
Moreover, the convergence of wireless sensor nodes with emerging technologies like blockchain could revolutionize data security and integrity. By utilizing blockchain for data transmission, organizations can ensure that the data collected is tamper-proof and verifiable. This combination of technologies would enhance trust in the information gathered by sensor nodes, particularly in critical sectors such as healthcare and environmental monitoring. As these advancements unfold, the potential applications and impact of wireless sensor nodes will continue to expand, shaping the future of connectivity.
Thanks
Wireless sensor nodes are redefining the landscape of connectivity in the digital age. Their ability to collect and transmit data in real time has opened new avenues for innovation across diverse industries. From agriculture to healthcare, these tiny devices are empowering organizations to make informed decisions based on accurate and timely information. The advantages of wireless sensor nodes, such as energy efficiency, scalability, and ease of deployment, make them an attractive solution for various applications.
However, challenges remain, particularly in terms of connectivity, battery life, and security. Addressing these concerns is essential for maximizing the potential of wireless sensor nodes and ensuring their widespread adoption. As technology continues to advance, we can expect to see significant improvements in the functionality and security of these devices, paving the way for even more innovative applications.
The integration of wireless sensor nodes into the Internet of Things marks a significant step toward a more connected and intelligent world. With real-world case studies highlighting their transformative impact, it’s clear that these devices are not just a technological trend but a vital component of our future. As we look ahead, the possibilities for wireless sensor nodes are limitless, promising to enhance our quality of life and drive significant advancements across various sectors.
What do you think?
The discussion is open! What are your thoughts? In your opinion, which of these technologies will play the most important role in the future of IoT? Every contribution is valuable and enriches the discussion.